First off, apologies for not have posting anything in the last few weeks. I just got back from Manila, Philippines to visit my ill grandfather (read: father). He made it, but is still weak. I love you lolo!
Anyway, I personally run Red Hat Enterprise Linux 4 at work for any *nix tasks, and in this post I’ll show you how to install Yum for easier management.
According to Linux@DUKE: Yum is an automatic updater and package installer/remover for rpm systems. It automatically computes dependencies and figures out what things should occur to install packages. It makes it easier to maintain groups of machines without having to manually update each one using rpm.
So, without further adieu:
1. Download yum-2.0.8-1.noarch.rpm from:
http://linux.duke.edu/projects/yum/download/2.0/yum-2.0.8-1.noarch.rpm
2. Install it with the following command:
rpm –i yum-2.0.8-1.noarch.rpm
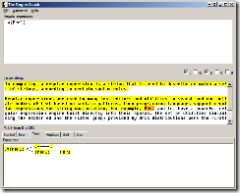
3. Configure your yum.conf [in /etc/yum.conf] like so:
[main]
cachedir=/var/cache/yum
debuglevel=2
logfile=/var/log/yum.log
pkgpolicy=newest
distroverpkg=redhat-release
tolerant=1
exactarch=1
#base]
#ame=Red Hat Linux $releasever – $basearch – Base
#aseurl=http://mirror.dulug.duke.edu/pub/yum-repository/redhat
/$releasever/$basearch/
[base]
name=CentOS-$releasever – Base
baseurl=http://mirror.centos.org/centos/4.4/os/i386/
gpgcheck=1
[updates]
name=Red Hat Linux $releasever – Updates
baseurl=http://mirror.centos.org/centos/4.4/os/i386/
gpgcheck=1
4. Download the GPG key for CentOS RPM packages with:
wget http://mirror.centos.org/centos/RPM-GPG-KEY-CentOS-4
5. Import the key like:
rpm –import RPM-GPG-KEY-CentOS-4
6. Run yum -y update, sit back, relax, and enjoy watching your system being updated.
That’s it! Now you can use yum to install anything you wish. Ciao!