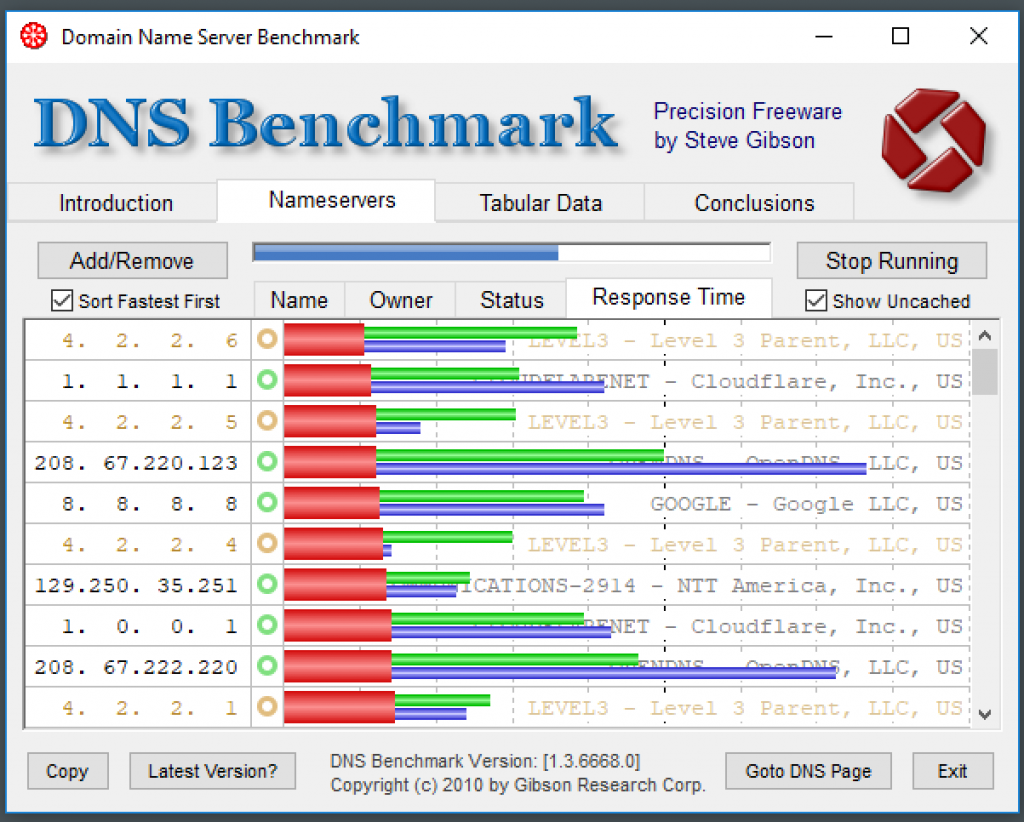
If you’ve been a techie for a long time, you’ll know who Steve Gibson from GRC is. His tools are mostly built in Assembly, so it’s rocket-fast. (One thing to note is they’re only for Windows.) For this post, I’d like to share the tool I use to identify which DNS servers I should use, as usually, our ISP’s servers are not the quickest. I get better response times when I specify the servers to use on my router.
You can download it from here. Give it a go!