My friend Anthony was getting “access denied” and “logon failure” errors when trying to to run psexec (from one of the PsTools suite) from an XP machine on a domain to an XP machine in a workgroup. It was something similar to:
PsInfo 1.34 – local and remote system information viewer
Copyright (C) 2001-2002 Mark Russinovich
Sysinternals – www.sysinternals.com
Could not connect to machine_name:
Access is denied.
And…
PsInfo 1.34 – local and remote system information viewer
Copyright (C) 2001-2002 Mark Russinovich
Sysinternals – www.sysinternals.com
Couldn’t access machine_name:
Logon failure: unknown user name or bad password.
Here are the settings/steps I checked/took that resolved the issue:
1. ping – was able to ping the machine by hostname. So no problem here.
2. net share – verified the ADMIN$ share was enabled. Again no problem here.
3. Remote Registry service – verified the service was started because the PsTools suite makes use of RPC calls via port 445. Was fine here.
4. Administrator password – verified the Administrator did not have an empty password. Was set here.
5. Test account – created a test account to use for psexec (e.g., psexec \\computer_name notepad.exe -u test -p test). Was available here.
6. Access hidden share – tried to access C$ and found that user name field grayed out. This tipped off the problem – cool!
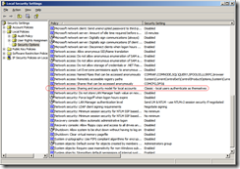
To fix it, I had to set the Network Access: Sharing and security model for local accounts security option Classic – local users authenticate as themselves.
Access it via Start > Run > secpol.msc > Local Policies > Security Options (see screenshot below).
Apparently, updates to Windows XP now sets this security option to Guest only – local users authenticate as Guest, which denies the ability to implicitly or explicitly use of a specific user name/password combo.
Hope this helps someone out there. Peace.
Ohhh man, thank you i was searching for this solution for ages…. I had to change Network Access: Sharing and security model for local accounts …. Once again THANKS a lot ….
That’s great, this problem has had me scratching my head for ages!!!
I have another small problem related to this. I have over 600 machines that require this setting changed. Is there a way of changing the security options by command prompt/batch file?
You most likely can accomplish this by changing the registry key below to ‘0‘ via a Windows PowerShell script. Check out the Group Policy Cmdlets; Set-GPRegistryValue might be it.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\forceguest
Excellent! Thanks for posting!